
If we’re to pinpoint a combat with out an finish or a particular winner, that may be the combat between cybersecurity consultants and cybercriminals.
It is a unending problem.
As expertise advances, criminals who search to use vulnerabilities have gotten extra inventive. On the opposite aspect, organizations have gotten extra cautious – and able to staying forward of the ever-changing digital threats.
With no proactive strategy, a single assault may cause your corporation to halt its operations – and even trigger its failure. We’re speaking a couple of fortune in fines, enterprise income, and authorized charges, to not point out the mark this may go away on a model’s popularity.
The dangers immediately are massive, extra quite a few, and extra versatile than ever. To guard your corporation and keep forward, you want a proactive strategy to cybersecurity and a strong resilience technique.
On this put up, we’ll educate you why this issues and how one can obtain it.
Understanding digital threats
A ransomware assault takes place each 40 seconds immediately.
On common, cybercriminals create 1.4 million web sites for phishing per thirty days, most of which comprise pages that mimic an actual firm – similar to yours.
So, we’re round 2,200 estimated cyber assaults each single day! What does this inform us?
This goes to point out that digital threats are right here, and they’re extra quite a few and profitable than ever. Right this moment, when most companies want expertise to progress and succeed available in the market, cybercrime is likely one of the largest threats to their success.
The results of a digital assault can range from minor to devastating for a enterprise. In case you are hacked, your organization’s data and that of your prospects can find yourself within the unsuitable palms.
You may get into authorized bother and pay authorized charges that may value billions! To not point out, relying on the assault and its success, this may flip a really profitable enterprise into ash.
It additionally is dependent upon the kind of assault, in fact. Some assaults are way more harmful and dear than others.
Ransomware assaults, for example, are very frequent these days, and these criminals have reached even the most important manufacturers on the market.
EXAMPLE: In July 2020, GTW World, an enormous US journey companies firm, made an infinite ransom fee – $4.5 million in Bitcoin to Ragnar Locker, a cybercrime ransomware group. The assault took down 30,000 computer systems and compromised tons of knowledge, together with safety documentation, monetary information, and staff’ private knowledge.
One factor is for sure: cyberattacks know no bounds, and each firm can fall prey to 1, or many. Nonetheless, you probably have an ingrained coverage and take a proactive anti-fraud strategy, you possibly can mitigate most of the dangers and may have a backup plan to fall on if issues go unsuitable.
What’s the most typical type of digital assault utilized by hackers immediately?
The menace panorama is shifting as expertise progresses.
The threats you fought only a few years again are extra versatile and superior now, and new threats are gaining energy with each passing minute.
Supply: Sprintzeal
With that in thoughts, listed here are the most typical sorts of safety threats immediately:
1. AI-powered assaults
Effectively, criminals certain love the advances in synthetic intelligence (AI).
They use it greater than ever. In line with a report by Sapio Analysis and Deep Intuition, the rise in assaults within the final couple of years is generally led by way of AI, with 85% of attackers utilizing generative AI.
The vast majority of assaults lately are facilitated by bots and different merchandise of synthetic intelligence. Cybercriminals use AI to automate every part from phishing to produce chain assaults.
2. Ransomware assaults
Ransomware assaults lately are extra focused and, subsequently, extra harmful. Attackers now encrypt knowledge and demand fee to maintain it personal.
Among the ransomware assaults are so well-planned and executed, that they value companies thousands and thousands. NotPetya, the largest ransomware assault to this point, made a financial affect of $10 billion and impacted main firms.
3. Provide chain assaults
When cyber criminals goal your organization’s provide chain, they’re performing a provide chain assault. If they’re profitable, they’ll fully infiltrate your community, and also you gained’t even discover it till it’s too late.
On this case, criminals infiltrate trusted distributors and use them to compromise the software program and attain the top customers. The potential harm has no limits.
4. Phishing assaults
Phishing has been round for a very long time, and it stays one of many primary methods criminals take over web sites. On this case, the hacker will ship a misleading message disguised as an electronic mail from an actual entity, requesting that the recipient reveal their login particulars.
In different phrases, they’ll faux it’s your firm sending a message to a buyer or an worker, demanding their login particulars or fee data. With the info readily available, they’ll use it to log in and do their harm.
In line with Statista, 76% of companies have reported being a sufferer of such an assault in 2022 alone.
Supply: Statista
5. DDoS assaults and SQL injections
Distributed denial of service (DDoS) assaults happen when criminals use a number of gadgets to hit a server with pretend visitors. The outcome? The web site turns into inaccessible and can’t perform usually. The assault paralyzes a server by overloading it and, in lots of instances, makes a web site go offline.
This may be devastating for large companies with a number of visitors since they lose through the downtime. There have been studies of main e-commerce platforms struggling such downtimes, even within the busiest intervals.
Equally, SQL injections enable hackers to entry your knowledge and shut it down. They inject SQL instructions into current scripts, and once they succeed, they’ll execute quite a lot of instructions – together with shutting it down altogether.
Supply: Spiceworks
6. Malware assaults
Malware assaults have been round for the longest time, however they continue to be probably the most widespread cyberattacks on the huge internet. Malware is malicious software program or virus designed to in some way hurt your computer systems, servers, networks, or shoppers.
In truth, any sort of malicious software program that serves the aim of harming or exploiting a programmable community or system falls underneath the “malware” class.
Digital threats: How you can stop, detect, and mitigate future assaults
Whereas digital threats now come hooked up to the usage of expertise and the web, and eliminating them altogether is not possible, there are some measures you possibly can take to forestall, detect, and mitigate them.
Extra particularly, you want what we name a cyber resilience technique – and right here is how you can create it.
Safe your knowledge – and carry out knowledge backups
The rule of thumb in cyber safety is to forestall it when potential. It’s all the time higher and cheaper to forestall a menace than it’s to repair the harm.
So, begin by securing your knowledge.
In case your knowledge isn’t as safe as it may be, that is the right time to go for a safer possibility. Begin by transferring knowledge and sources to a safer infrastructure or a unique software program i.e., carry out a system migration. Simply make sure you optimize the system migration course of and maintain it as secure as potential.
Subsequent, it’s time to again up all the info. That is a part of your restoration plan – you may have one other location for the necessary data in case it will get misplaced, or your corporation falls sufferer to a cyber assault.
Knowledge backup is common work – not a one-time measure. Usually again up techniques and important knowledge utilizing quite a lot of options similar to exterior onerous disks and cloud-based software program.
Defend your self from authorized bother
Knowledge safety legal guidelines change daily.
They regulate thousands and thousands of companies to be able to shield prospects. In case of an information breach or some other cyber assault, you should guarantee that your corporation is compliant with present rules to keep away from hefty authorized charges and issues.
Whereas there are many methods to stick to the altering knowledge privateness legal guidelines’ necessities, some practices are extra widespread than others, similar to the usage of the banner cookie.
Cookie banners are a technique to meet the necessities unobtrusively. They seem as a pop-up when individuals go to your web site, informing them about the usage of cookies and asking them for consent.
When the customer accepts the cookies and the storage and use of their knowledge, you’re legally lined. It’s nonetheless your accountability to guard that knowledge but when a breach happens and also you’ve taken the required measures to forestall it, you at the very least gained’t have to consider authorized penalties.
Have a digital assault response and restoration plan in place
Backing up knowledge is simply step one in every of your restoration plan. In lots of instances, it gained’t matter you probably have the info saved some place else whether it is already compromised.
So, how are you going to create an incident response plan?
An incident response plan contains a number of components:
- Preparation: Doing no matter potential to forestall any incident from taking place
- Incident detection: Discovering out what the issue is
- Incident containment: Ensuring that the harm doesn’t get greater
- Restoration: Mitigating the state of affairs to the very best of your capacity
Merely put, a cyber incident response plan is a doc, a plan that outlines what your organization would do within the occasion of a safety incident similar to an information breach.
Most of the cyber assaults are unavoidable, even you probably have a wonderful safety system in place. Nonetheless, such a plan provides you with one thing to work on – an motion plan, in case you’d like.
The response plan may have pointers to your group to take earlier than an incident happens. Then, it should comprise steps that it must take to determine when the techniques or knowledge are compromised.
Subsequent, it provides you with concepts on how one can mitigate the harm if and when it happens. And at last, it provides you with a plan on how you can recuperate from several types of cyber assaults. 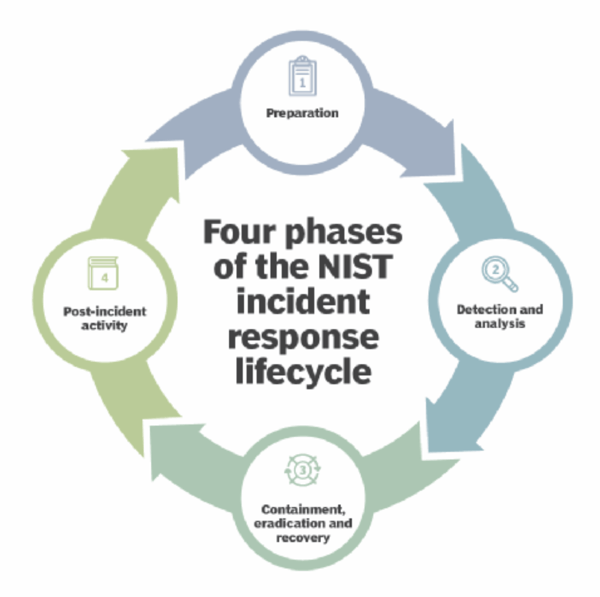
Supply: TechTarget
Conduct steady monitoring
Cyber threats are finest handled whenever you catch them in actual time. Nonetheless, with so many threats and makes an attempt, it’s not possible to maintain observe of every part – and spot each little glitch that signifies an assault.
Companies and cybersecurity professionals have an excellent set of instruments at their disposal for real-time menace detection. A lot of the threats are avoidable in case you catch them earlier than they penetrate your safety system, and instruments like internet proxies and bot detection can assist you do that continuous, with none human effort.
You may take a look at and consider your digital presence and knowledge by utilizing monitoring and evaluation instruments and companies. These will routinely conduct vulnerability assessments, penetration testing, and safety audits to deal with any vulnerabilities in your corporation’s digital merchandise, similar to a web site or an app.
Carry out worker coaching
Do you know that 88% of knowledge breach incidents are attributable to an worker who made a mistake?
Until you prepare your staff and educate them how you can combat off digital threats, your corporation is at hurt. It doesn’t matter how nice of a software program you’ve invested in to trace and mitigate assaults or how thorough your restoration plan is – a single worker can go away the digital door open for hackers, usually unintentionally.
That is why, immediately, greater than ever, you will need to educate your employees on widespread digital threats, how you can determine them, and the way to answer them. Consider your staff as the primary line of protection you may have towards cyber criminals. It’s your accountability to coach them on the subject to forestall hackers from utilizing your workforce to hurt the enterprise.
Encryption and knowledge safety
Whereas amassing and utilizing consumer knowledge is roofed with consent, it’s nonetheless your accountability to encrypt that knowledge and maintain it secure. Methods like encryption defend delicate data towards cyber assaults and brute drive assaults like ransomware and malware.
Merely put, you’d be translating all delicate knowledge into code or one other kind in order that solely the individuals who can learn will probably be capable of entry it.
Common evaluations and updates
Cyber resilience is a piece in progress.
You may’t merely create an incident response or restoration plan, spend money on some software program options, and overlook concerning the matter.
Criminals are extra inventive with each passing day, which implies that the methods you employ immediately would possibly now not work tomorrow. With that in thoughts, it’s best to usually assessment and replace your technique to align with new digital threats and the trade’s finest practices.
The advantages of a robust cyber resilience technique
Whenever you take measures to detect, stop, and mitigate cyber threats, you’re forming your cyber resilience technique. Listed below are among the the explanation why that is necessary:
Enhanced safety
technique protects your group towards digital threats. It contains every part from backing up the info, addressing vulnerabilities, and making ready for any potential cyber assaults.
Aggressive edge
Despite the fact that digital threats are extra quite a few than ever – and way more harmful than earlier than, most companies function on the premise that they’re too small for cybercriminals to focus on them or that their previous methods labored thus far, so why wouldn’t they now?
Because of this most of your competitors may have outdated or poor cyber resilience methods in place – if any. In line with an UpCity ballot, 50% of companies don’t have a cybersecurity plan in any respect.
This provides you a wonderful aggressive benefit. For starters, you’re much less prone to turn into a sufferer of a cyber assault. However you can too present the audience that you’re devoted to strong practices and place your self as a extra dependable, reliable associate.
Stronger popularity
A robust cyber resilience program safeguards the popularity of your corporation. In the event you do that constantly, it should foster belief amongst your prospects, in addition to your companions and stakeholders.
A stronger popularity in a aggressive market is every part. It equals extra prospects, stronger partnerships, and, in fact, extra income.
Compliance with rules and legal guidelines
As we talked about, legislation compliance is essential in terms of knowledge safety and privateness, and in case you fail to stay compliant, you’re looking not solely at knowledge leaks and hacks however at penalties and authorized issues, too.
Your cyber resilience program needs to be centered on trade rules and requirements above every part else to make sure that, at any given second and in any state of affairs, your corporation is compliant with the present legal guidelines.
The price of being non-compliant is almost 3 times larger than the price of being compliant lately. On common, the value of compliance is $5.47 million in comparison with $14.82 million for non-compliance.
Supply: Fortra
Enterprise continuity
Whereas not all cyber assaults are avoidable, a great safety plan and methods can assist you keep away from most of them. For any digital menace you efficiently stop or mitigate, you’re making certain enterprise continuity and success.
Let’s say that you simply handle to guard your corporation from a ransomware assault that may in any other case value you thousands and thousands – or damage it altogether. You simply helped your corporation survive. Let’s say you averted countless phishing assaults or malware attempting to get to your knowledge. Congratulations, you’ve efficiently safeguarded your monetary stability and your popularity.
In the event you stop a DDoS assault or an SQL injection, you possibly can preserve a seamless workflow and forestall main losses.
Future-proofing your cyber resilience plan
Right this moment, not taking your corporation on-line is an enormous drawback. In truth, usually, companies should go browsing to succeed in their focused viewers and make gross sales. Nonetheless, with this benefit come many dangers, most of them within the type of digital threats.
Digital threats are in all places – and it’s your accountability to guard your corporation. It’s your activity to create a fierce cyber safety resilience technique, implement it, and maintain it always up to date.
Digital threats evolve and alter extra incessantly than anybody can comply with. That being mentioned, it’s your job to maintain up with the adjustments in cybercrime in addition to cybersecurity methods. To be one step forward, you positively wish to think about predictive tendencies and imminent dangers, particularly with the rising reputation of AI and distant work.
Synthetic intelligence and machine studying give cybercriminals a plethora of choices in terms of concentrating on companies.
Irrespective of how massive or small your organization is, the danger is all the time current. Don’t suppose, “there’s no manner they’ll trouble hacking my enterprise.” That is what many of the firms that fell sufferer to digital assaults thought prior to now!
Get a cybersecurity deep dive with Dr. Chase Cunningham as he talks about Zero Belief.